What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting and Conformance. It is a standard email authentication protocol that takes authoritative action in case DKIM and SPF authentication fail.
What is DMARC enforcement?
DMARC enforcement refers to the process of applying DMARC policies to ensure that emails failing SPF and DKIM checks are handled according to the defined policy.
Enforcement is crucial for preventing email spoofing and phishing attacks, as it dictates how receiving mail servers should process emails that do not meet authentication standards.
If you don't know about SPF and DKIM, we suggest you to read about them first.
DMARC performs the following functions:
Aligns with SPF and DKIM: SPF specifies which mail servers can send email on your domain's behalf. DKIM adds a digital signature to emails, which helps verify the email's origin. DMARC ensures that the domain in the "From" address aligns with the domains authenticated by SPF and DKIM. We will learn more about this further in the article.
Defines policies: DMARC defines policies that specify how receiving mail servers should handle emails that fail authentication checks. The policies include none (accept the message), quarantine (delivers to junk/spam folder), and reject (is not delivered).
Provides reports: DMARC provides domain owners with reports summarizing the email traffic and showing how emails from their domain are being authenticated. It also sends forensic reports, which provide detailed information about specific emails that fail authentication checks.
An organization can easily incorporate the DMARC protocol into its existing inbound email authentication process. The major goal of DMARC is to ensure that the email message aligns with the receiver's knowledge of the sender. If it doesn't match, proper guidelines are in place to handle such unauthenticated messages.
Before we jump into the technicalities of DMARC, here’s a glossary of frequently used terms to ease your journey with DMARC.
| Term |
Definition |
Purpose/Function |
| DMARC |
Domain-based Message Authentication, Reporting, and Conformance |
Protocol that allows domain owners to protect against email spoofing and phishing. |
| DMARC policy |
A set of rules specified in the DMARC record that determines how to handle emails that fail authentication. |
Directives for handling emails: p=none, p=quarantine, or p=reject. |
| DMARC enforcement |
The application of the DMARC policy by receiving mail servers based on the defined rules. |
Executes the actions defined in the DMARC policy. |
| DMARC alignment |
The requirement that the domains used in SPF, DKIM, and the "From" header match according to specified rules. |
Ensures consistency in sender identity, either strictly or relaxed. |
| Strict alignment |
A mode of alignment requiring an exact match between the "From" address and SPF/DKIM domains. |
Increases security by ensuring precise domain verification. |
| Relaxed alignment |
A mode of alignment allowing subdomains to pass authentication checks. |
Provides flexibility while maintaining some level of security. |
Why should you set up DMARC?
The importance of DMARC is deeply tied to email security and deliverability. Here's why you should authenticate emails with DMARC.
1. Identifies spammers quickly
The DMARC protocol helps ISPs (Internet Service Providers) identify spammers quickly by ensuring emails pass SPF and DKIM checks, align with the domain in the "From" header, and enforce policies to quarantine or reject unauthorized emails. This prevents malicious emails from reaching recipients' inboxes.
2. Protects from spoofing and phishing
DMARC aligns with SPF and DKIM to determine an email's authenticity. The protocol reduces phishing practices that deliver fraudulent emails to the recipient's inbox and further minimizes false positives and email malpractices.
DMARC also helps ensure that only legitimate senders can use your domain, reducing the risk of attackers sending fraudulent emails pretending to be from your domain.
3. Provides robust email authentication reporting
DMARC is the only authentication protocol that reports how incoming emails should be treated based on SPF and DKIM pass/fail status. So, if an email is DMARC authenticated, it indicates that the sender is legitimate and the content hasn't been tampered with.
How does DMARC work
As discussed earlier, DMARC relies on the validation status of SPF and DKIM, two of the most useful authentication protocols. Besides them, the Domain Name System (DNS) also plays a major role in DMARC validation.
Briefly, the process looks like this:

Every domain administrator has a DMARC policy that defines email authentication practices and how receiving mail servers should handle email if that policy is violated. This DMARC policy is listed in that domain's DNS record.
When a receiving mail server receives an incoming email, it uses DNS to look up the DMARC policy for the domain in the message's "From" (RFC 5322) header.
The receiving server then evaluates the message for three key factors:
Does the message's DKIM signature validate?
Did the message come from IP addresses allowed by the sending domain's SPF records?
Do the headers in the message show proper "domain alignment"?
With this information, the server then applies the sending domain's DMARC policy, which includes whether to accept, reject, or otherwise flag the email message.
After using the DMARC policy, the receiving mail server will report the outcome to the sending domain owner.
Note: The sender domain, as well as the envelope domain, must pass SPF. Or the sender domain is a sub-domain of the envelope domain or vice versa.
What is a DMARC policy?
A DMARC policy is a set of actions specified in the DMARC DNS record that tells mail servers how to handle emails that fail SPF and/or DKIM authentication checks. The values for the same are p=none, p=quarantine, and p=reject.
Here is what these tags individually mean:
1. Monitor-only policy; p=none
When the policy is set to p=none, no action will be taken on emails that fail authentication. Instead, the policy will deliver the email to the recipient's inbox and the report will be sent to the email address specified in the rua tag to monitor.
When to set this policy: It is recommended to set this policy when you first set up DMARC.
Note: you shouldn't change the policy from none to quarantine or reject until you understand which messages aren't authenticated.
2. Quarantine policy; p=quarantine
When the policy is set to p=quarantine, the email will be delivered to the junk/spam folder in case it fails the DMARC check. You will continue to receive reports.
When to set this policy: This policy can be set when you want to monitor the emails being authenticated but also prevent harmful messages from landing in your inbox.
3. Reject policy; p=reject
Besides sending DMARC reports, the DMARC policy instructs email receivers not to deliver emails failing the DMARC checks. They will simply be rejected by the mail servers. It will usually send a bounce message to the sender.
When to set this policy: It is recommended to keep this as an eventual or permanent option for your DMARC policies once the DMARC reports show that valid messages are authenticated and delivered to the inbox.
What does DMARC alignment mean?
DMARC alignment refers to the validation of the alignment between the domain used in the "From" address of an email (also known as the RFC5322.From header) and the domain used in other authentication mechanisms like SPF and DKIM.
In this process, a message will pass DMARC authentication based on how strongly the From header matches the sending domain specified by SPF and DKIM.
The From header is the email address in the message header. It contains information about the sender's name and email address.
There is also an envelope sender address, which the recipient cannot see. This is the email address where undeliverable and bounced messages will be sent. It indicates where the message came from.
In the context of DMARC alignment, there are two modes of alignment that can be enforced by DMARC policy: "strict" and "relaxed". These modes determine how strictly the domains in SPF and DKIM must align with the domain in the "From" header for a message to pass DMARC checks.
1. Strict alignment:
SPF strict alignment: In strict alignment, SPF alignment requires an exact match between the domain in the MailFrom (envelope sender) and the domain in the "From" header of the email. If the domains do not match exactly, SPF alignment fails.
DKIM strict alignment: DKIM strict alignment requires an exact match between the domain in the DKIM signature (d=) and the domain in the "From" header. If the domains do not match exactly, DKIM alignment fails.
Outcome: For DMARC to pass in strict alignment mode, both SPF and DKIM must pass and the domains in their respective headers must exactly match the domain in the "From" header.
2. Relaxed alignment:
SPF relaxed alignment: In relaxed mode, SPF alignment allows for a partial match between the domain in the MailFrom and the domain in the "From" header. This means that subdomains of the MailFrom domain are also considered valid.
DKIM relaxed alignment: DKIM relaxed alignment allows for a broader match, where the DKIM signature's domain (d=) can be a subdomain of the domain in the "From" header.
Outcome: DMARC can pass in relaxed alignment mode if either SPF or DKIM passes and their domains align in a relaxed manner with the domain in the "From" header.
Suppose the alignment is set to be relaxed. The header From address is kyle@yourdomain.com, and the envelope sender address is kyle@mail.yourdomain.com; DMARC will consider it a 'pass'. However, if it is set to be strict, it will fail.
You can specify how strictly the From Header or the message information should match the SPF and DKIM signatures. The values for the same are r and s.
You can add it to the DMARC record by using these tags: aspf and adkim.
What does a DMARC record look like?
A DMARC record is set up to define how strictly DMARC should check messages and recommend action when a message fails authentication checks.
A DMARC record is found in an organization's DNS database. A DMARC record is a specially formatted version of a standard DNS TXT record with a particular name, namely "_dmarc.mydomain.com"
Following is an example of a DMARC record:
_dmarc.mydomain.com. IN TXT “v=DMARC1; p=none; rua=mailto:dmarc-aggregate@mydomain.com; ruf=mailto:dmarc-afrf@mydomain.com; pct=100”
There are a total of 11 tags applied to a DMARC policy, out of which "v" and "p" tags are listed first. Other tags can be listed in any order. Here's what these tags mean:
v=DMARC1 specifies the DMARC version.
p=none tag is the policy (meaning what action to take if the message fails DMARC)
rua=[mailto:dmarc@yourdomain.com](email to:dmarc@yourdomain.com) tag is the email address to send DMARC aggregate reports to.
ruf=mailto:dmarc-afrf@mydomain.com is the mailbox to which forensic reports should be sent.
pct=100 is the percentage of mail to which the domain owner would like its policy applied
aspf tag represents alignment mode for SPF, meaning it determines how strictly the SPF check aligns with the domain in the "From" header.
adkim tag represents the alignment mode for DKIM. It defines how strictly the DKIM check aligns with the domain in the "From" header.
How to add a DMARC record to your DNS provider
After properly setting up SPF and DKIM, the DMARC policy will be tested and verified. Before DMARC is turned on, messages should be authenticated for at least 48 hours. The DMARC record must then be added to your domain's DNS settings.
Here's how you can set up the DMARC DNS:
1. Set up SPF and DKIM
Before setting up DMARC, ensure that your domain is correctly configured by SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). If you have multiple domains, set up SPF and DKIM for each separately. Skipping this step may cause deliverability issues.
2. Log in to your domain hosting platform
Firstly, you have to log in to your DNS hosting provider. Different servers have different interfaces. You can also go to the manage/configure DNS settings option. Once logged in, check for the 'Creating a new record' prompt.
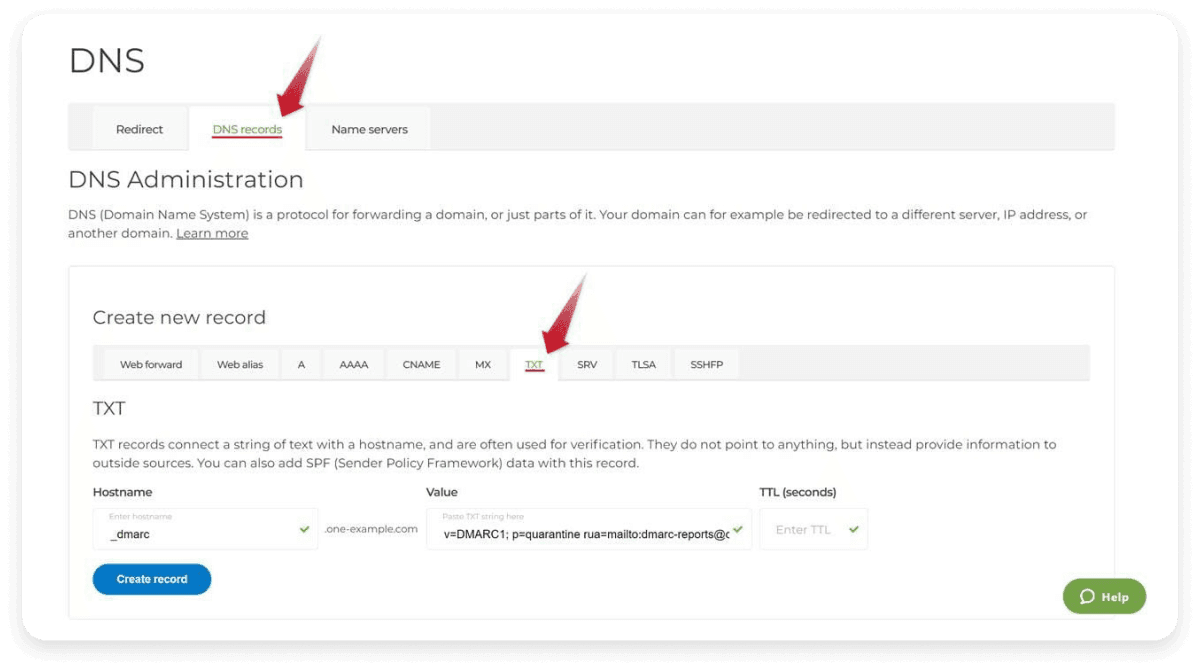
3. Create a new DMARC TXT record
Search for the 'TXT' section to create and edit a new record.
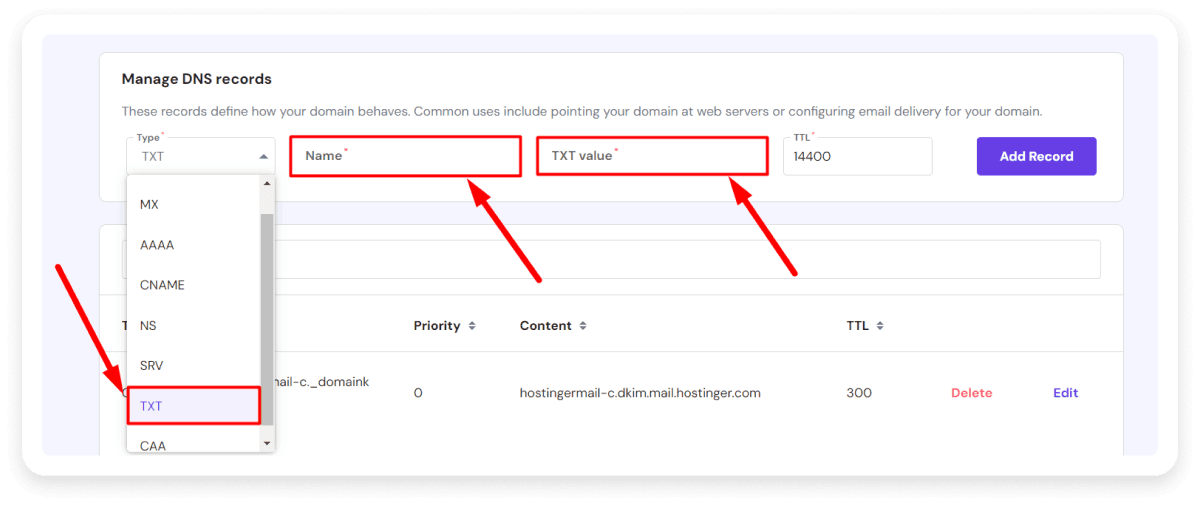
4. Enter the values
Next, you can fill in the values required to set up DMARC:
Host/Name: Input the value'_DMARC' in this column. If you enter a DMARC record for a subdomain, then put in '_dmarc.subdomain'. The hosting provider will add the domain or subdomain after the value.
Record type: Select the 'TXT' DNS record option from the drop-down list.
Policy: Every DMARC record requires two tag-value pairs. First is "v," and second is "p." The former "v" has only one tag-value pair provided as v=DMARC1. Three "p" tag pair options are usually available: ' none,' 'quarantine,' or 'reject.' The entry of these tag-value pairs will be: 'p=none,' 'p=quarantine,' or 'p=reject.'
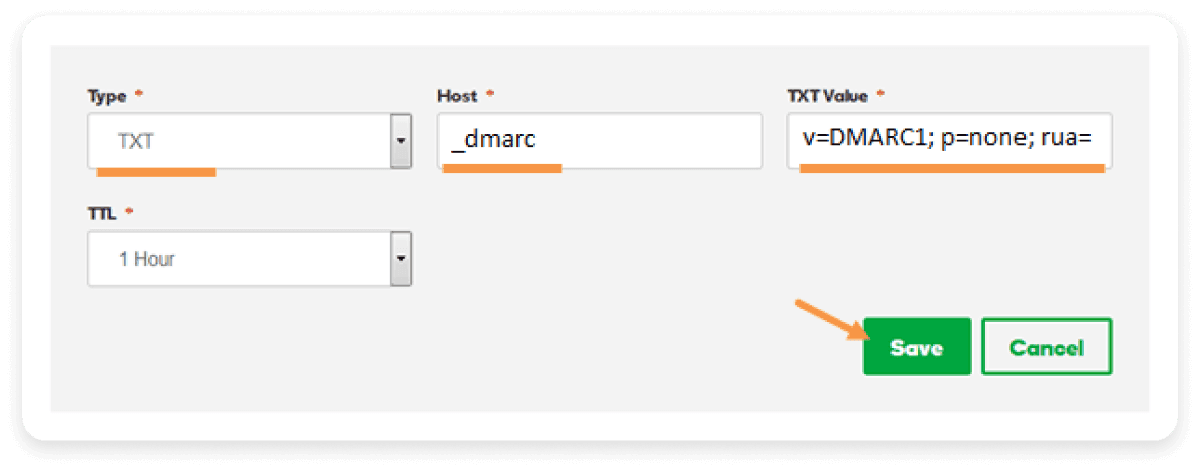
5. Tap on create/save
Click the create/save option to generate and submit the DMARC record.
6. Validate the record
The step involves direct testing of the new DMARC record. Check and verify the syntax and values added are working correctly. Test all the defined policies to ensure they are performing as required. Hence, there's no scope for any legitimate email to get blocked.
Common misconceptions about DMARC enforcement
- "DMARC is a one-time setup"
Clarify that DMARC requires ongoing management and adjustment. As email practices evolve, regular monitoring and updates to the policy are necessary.
- "Enforcement is only for large organizations"
Emphasize that DMARC is beneficial for any domain, regardless of size. Smaller organizations can still be targeted for phishing and spoofing, making enforcement vital.
You can check the status of your DMARC authentication using the following DMARC checker tools:
1. DMARC Checker by Mailmodo
Mailmodo's DMARC Checker ensures your email security by analyzing your domain's DMARC records. Simply enter your domain, click "Check DMARC," and review the results to see your email policies and any issues. This helps maintain your email authenticity and improve your domain's security.
It also validates the DMARC records and highlights any errors, such as missing records or syntax issues.

2. Mimecast DMARC Analyzer
Mimecast is one of the pioneers of DMARC, and its analyzer tool is one of the best for tracking DMARC authentication. The tool offers a 14-day free trial; you can then ask for a quote based on the features you'll be using.

3. Glock Apps
Glock Apps is a free DMARC analyzer tool that offers 10,000 DMARC messages monthly. However, if you want more advanced features, you can get their paid plans, starting at $15.

4. Dmarcian DMARC Report Analyzer
Dmarcian will make the DMARC report easy to read and analyze to identify how emails are sent and from your domain. It offers a 14-day free trial without any credit card requirement.
DMARC checker by MxToolBox is simple and free to use, as all you have to do is upload an XML file of your DMARC record. The tool will make the file human-readable by parsing and aggregating them by IP address into readable reports.

Get your domain DMARC approved by Mailmodo
With Mailmodo, you can easily set up DMARC and send interactive AMP emails. The Mailmodo team assists you in incorporating the DMARC to protect your company's domain name easily and reap the benefits of interactive AMP emails.





























