What is email fraud?
Email fraud is a deceptive practice that uses emails to mislead individuals or organizations for personal gain or to cause harm. It aims to obtain one of two things or both- money or sensitive information such as passwords, usernames, credit card numbers, and financial information.
A popular example of email fraud is the Nigerian Prince email scam. In this scam, the scammer convinces the victim to pay a small fee with the assurance of receiving a large sum of money later. Here’s what the Nigerian Prince email looks like.
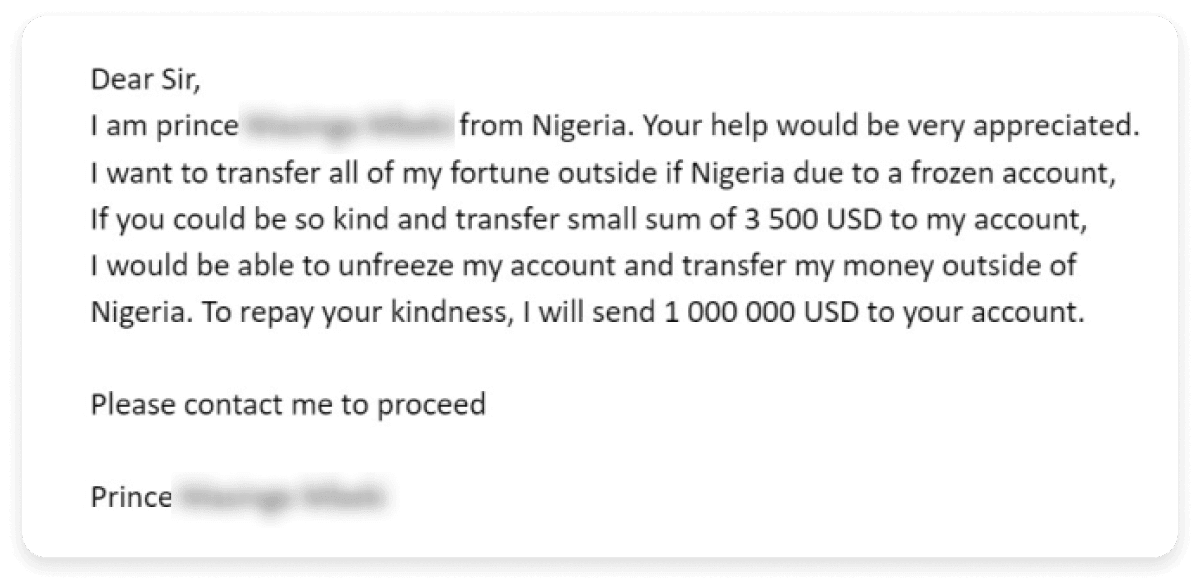
Types of email fraud
Understanding different types of email fraud is important for identifying and overcoming the threats that come with them. Some of the common types of email fraud include:
Phishing
Phishing attack is an email fraud in which scammers send deceptive emails to people and trick them into sharing their personal details, such as passwords and credit card details. This is usually done by pretending to be trustworthy entities, such as banks or government bodies.

Phishing can be of various types depending on the method the scammer uses to exploit the victim, the target, and the channel used, e.g., email, phone call, or text message.
Spear phishing: Spear phishing targets specific individuals or organizations by personalizing the email to make it look as if it’s coming from a trusted source. It aims to trick the victims into downloading malware or transferring funds.
An example would be an email that appears to be from your boss, requesting you to transfer some funds to an account urgently.
Whaling: Whaling targets high-profile individuals, such as CEOs and senior executives of companies, to get them to reveal sensitive information or approve large financial transactions.
Vishing: In vishing, scammers make phone calls pretending to represent legitimate organizations such as banks or companies. They fool people into sharing bank details, passwords, and credit card details.
Smishing: Smishing uses SMS (text messages) to deceive people into disclosing sensitive information by tricking them into clicking on bad links in SMS or replying to text messages with personal details.
A message displaying that there is an issue with the bank account of the receiver and asking him to click a link to verify information is a perfect example of smishing.
Note: Vishing and smishing aren't exactly types of email fraud, but they are still forms of phishing.
- Advance-fee scam: An advance-fee scam is a fraud where an attacker persuades individuals to pay an upfront fee for benefits such as a large amount of money or gift. Once the individual pays, the scammer finds new ways to obtain more money or disappears.
While there are other types of phishing emails too, these are the most commonly found ones.
💡 Related guide: What Is a Phishing Emails, Its Types, and How to Report It
Spoofing
Spoofing is an email fraud technique in which the scammer changes the email header (sender details) to make it appear that the email has come from a credible source. This method intends to convince the recipients to open attachments, click on harmful links, or disclose sensitive information.
Take a look at the image that shows two emails in which the sender detail appears to be the same but it actually isn’t.
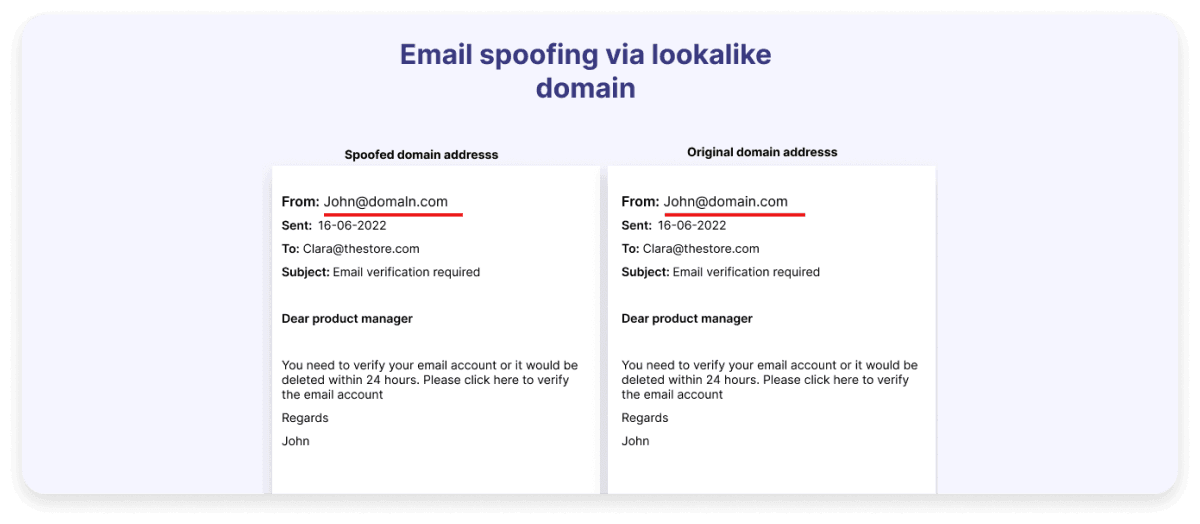
Spoofing can take various forms depending on the method used to deceive the victim, the target, and the medium involved, such as email, phone calls, or websites.
1. Email spoofing: Email spoofing involves sending emails with false sender addresses to steal your information and harm your computer with malware.
Here’s an example of email spoofing, where the scammer sends an email that appears to be from PayPal. The message warns the user that their account will be permanently disabled unless they click on the provided link. If the user is tricked and enters their information, the attacker can gain access to their PayPal account and steal money.

2. Website spoofing: Website spoofing includes creating a fake replacement of a valid website to deceive users. The users believe they are interacting with the original website when they aren’t.
The below image shows the difference between real and spoofed websites based on their URLs. The legitimate website displays a secure and correctly-spelled URL, while the spoofed website has a fake URL that is similar to a real URL but has slight variations to mislead people.

Email spoofing can be done in one of the following ways:
Spoofing via lookalike domain: Scammers create a domain name that closely resembles the original domain as we saw in the example above. For example, a scammer might use paypa1.com instead of paypal.com.
Spoofing via display name: Scammers change the display name of the sender to mimic the name of a genuine or trusted person. For instance, they might change the name of the sende’s name to Elon Musk to deceive the recipient into thinking the email is from a credible source.
Note: Website spoofing isn't classified as email fraud, but it falls under spoofing.
💡 Related guide: What Is Email Spoofing and How to Safeguard Against It
Malware distribution
Malware distribution via email involves sending emails that contain malicious software as attachments. Users might receive emails that appear legitimate and are tricked into clicking harmful links and downloading infected attachments.
The attachments often disguise malware as Word documents or PDFs. In other cases, clicking on infected links can automatically download malware on your system, allowing attackers to steal information or gain unauthorized access.
How to protect yourself
Protecting yourself helps maintain the privacy and confidentiality of your information against various threats, such as phishing and spoofing. Here’s how you can safeguard yourself against these.
1. Identify and avoid suspicious emails
Identifying and avoiding suspicious emails is important for protecting yourself from various online threats. Recognizing the signs of a fraudulent email can safeguard your sensitive data and prevent potential security breaches. Here’s how to identify these emails:
Always verify the sender’s email address to ensure it comes from a trusted source. You can do this by checking for misspellings or unusual domains.
Check for authentication, such as verified sender or secure email signatures.
At times, email clients flag suspicious emails and send you warning messages. Be aware of these messages to prevent potential threats.
If you find the email message to be suspicious, search the email content on the Internet to see if similar messages were used to trick people or if others have reported similar scams.
Scammers often create a sense of urgency, so if an email pushes you to act fast, take your time to inspect the email.
Avoid downloading attachments from unknown or unexpected sources, as they may contain harmful content. If an email asks for payment details or money, double-check its authenticity.
2. Enable multi-factor authentication
Multi-factor authentication offers a high level of security when logging into online accounts. It demands the users to input a code or verify their login from a different device, apart from entering their username and password. Some other means include answering secret questions or scanning fingerprints. This two-factor authentication prevents unauthorized access if the system or device password has been stolen.
Multi-factor authentication offers high security, reduces the risk of unauthorized access, and protects against phishing and other email fraud. Even if an attacker manages to obtain your password, they still need an additional authentication factor to access your email account, reducing the risk of unauthorized access.
3. Use email security software
Email security software safeguards email content from unauthorized access and email fraud. They offer advanced features such as spam filtering, data protection, and email encryption. They block unwanted or harmful emails, lowering the risk of email attacks. By encrypting the email content, they ensure the email is not altered during transmission, protecting the integrity and confidentiality of the message.
Some of the best security software include:
Proofpoint Essentials
Barracuda Email Security Gateway
Trend Micro Email Security
Microsoft Defender for Office 365
Cisco Secure Email Threat Defense
Avanan
Virtru
Cofense PDR
4. Implement email authentication protocols
Implementing email authentication protocols such as SPF, DKIM, and DMARC protects your domain from being used in email fraud. Here’s how:
SPF: Sender policy framework (SPF) verifies if the sending email server is authorized to send emails on behalf of your domain.
DKIM: DomainKeys identified mail (DKIM) ensures the email content was not modified during transit by adding a digital signature in the email header.
DMARC: Domain-based message authentication, reporting, and conformance (DMARC) defines how an email must be handled if it doesn’t pass authentication checks.
💡 Related guide: Understanding Email Authentication Protocols: SPF, DKIM, and DMARC















