11 phishing email examples and common warning signs
As scammers find more and more innovative ways of phishing, it is vital to be aware of some common phishing techniques and ways to point them out. Here are some examples of the most common types of phishing emails and what you should watch out for to identify their malicious nature.
1. Account hack claim
The below email claims that the recipient’s device has been hacked and that the hacker has complete access to the recipient’s device, including its display and camera. The email goes on to threaten the user that if a given sum is not paid as ransom, all the data of the recipient will be disclosed to the public. While in very rare cases, the sender might be a real hacker, in most cases, these emails are phishing attempts. They expect the sender to get worried and send the ransom money to the sender.
Why this email is suspicious:
- The email is vague, with no proof of hacking.
- The email doesn’t specify any information about the recipient.

2. Refund from college email
The following email is apparently from a company called BankMobile Disbursement and claims that they work with the recipient's college to deliver a refund. The email asks the recipient to click on a button to claim the refund, which redirects them to a page that asks the user for their bank details. Providing these details can empower scammers to steal money from the recipient’s bank account.
Why you should be suspicious:
- The email is sent from an external address.
- No details about the company are provided.
- The sender asks for bank account information.
- There is no information from the college about any refund.

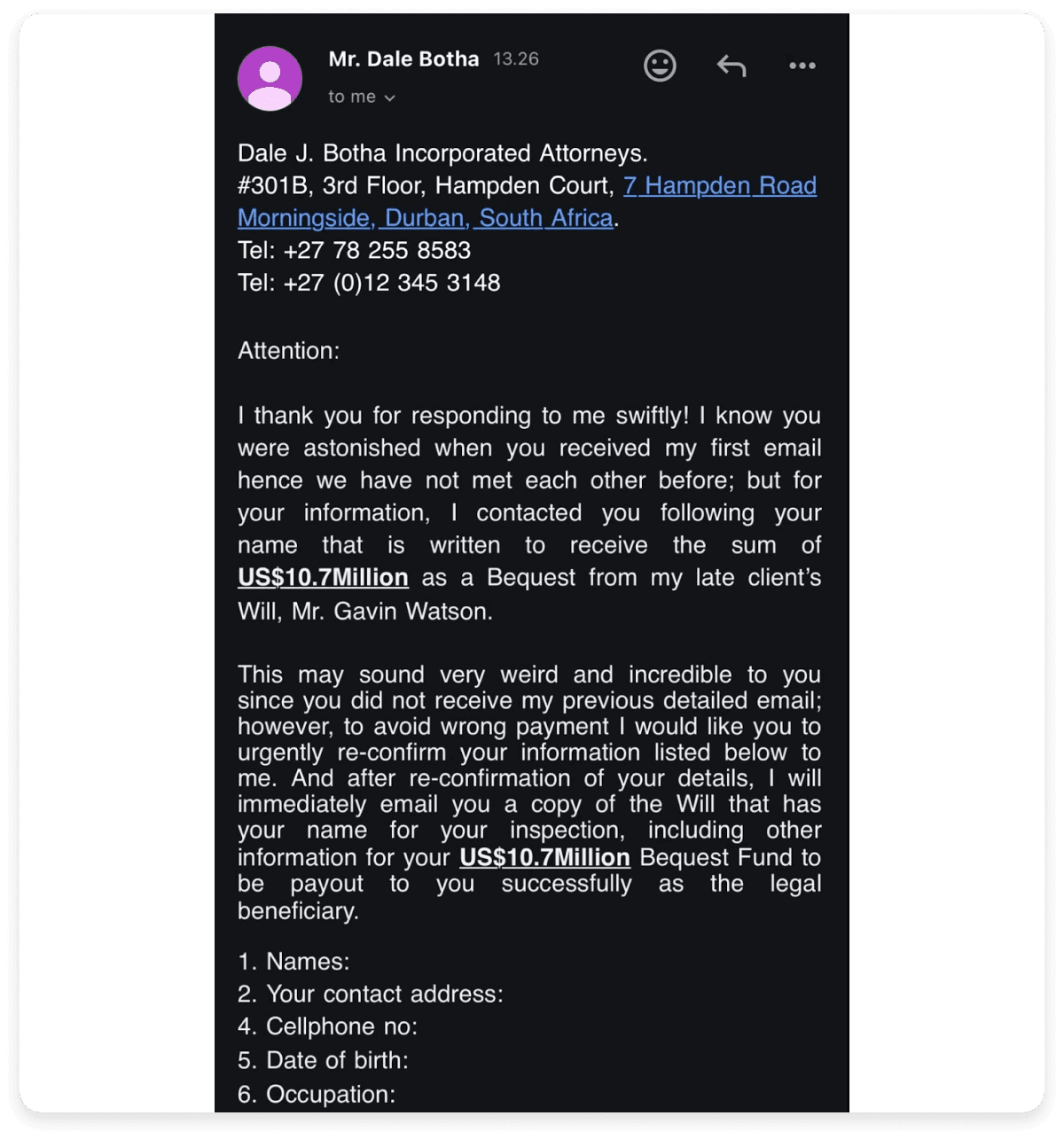
3. Will inheritance email
The following email claims that the recipient has inherited a large sum of money according to the will of the sender’s late client. It also asks for some personal details of the recipient so that the will can be sent to the recipient and the money can be paid. Once the scammer gets access to the personal details of the sender, these details can be used for various purposes, including getting credit cards under the user’s name.
Why you should be suspicious:
- The email promises easy money and is too good to be true.
- The deceased person is a stranger to the recipient.
- A copy of the will is missing from the email.
- The information requested about the recipient should have been there in the will.
4. Partnership proposal email
The phishing email below claims that it is an inquiry for a partnership proposal. The body of the email asks the recipient if they are still active on that email address and contains an attachment which is a .dat file. These file types can contain video, audio, PDF, and virtually any other type of file. The user is expected to reply to the email, which prompts a thread of emails. As a result, the user is tricked into revealing personal information to the scammers.
Why you should be suspicious:
- The body of the email is very vague and contains no details.
- The attachment can be malicious and can contain malware.
- The sender has attached a file instead of just typing the email address, which would have been much easier.
- The list of participants in the email thread is not revealed.

5. Subscription expired email
The following phishing email makes use of spoofing. The recipient is informed that their Netflix subscription has expired and that their payment details have to be updated. It also makes it look like the email is providing the information related to the recipient’s account but it’s not really doing so. For instance, the entire email address is replaced by asterisks except for the domain name. The CTA button leads to a fake webpage that collects the user’s payment details and transfers money into the scammer’s account.
Why you should be suspicious:
- The Netflix logo is missing.
- No details of the user’s account are provided.
- The email body has unprofessional formatting.

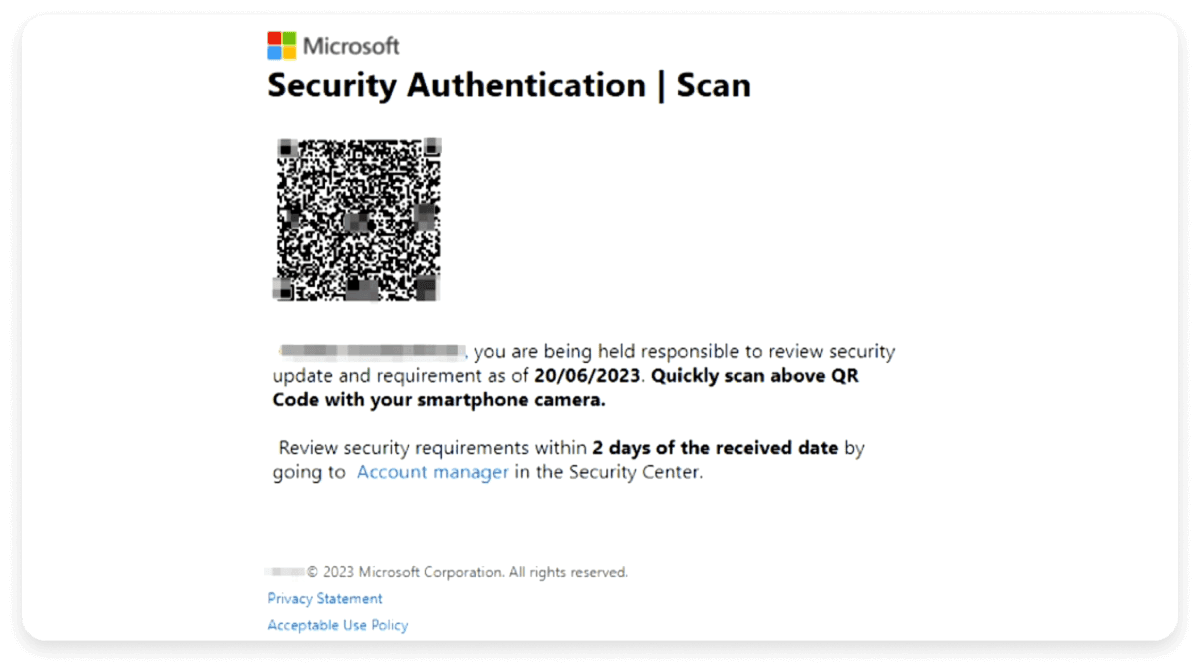
6. Security authentication QR scam
The following email is an example of a QR phishing scam. The email pretends to be from Microsoft and provides the user with a QR code to complete a security authentication. It even tries to create a sense of urgency by asking for immediate action. Once the user scans the code, they are redirected to a bogus website that asks them to enter their login credentials and payment information in the pretext of updating the account. This can lead to the user losing money to the scam.
Why you should be suspicious:
- No proper details of the user’s account are provided.
- It creates a sense of urgency.
- Companies don’t ask you to scan a QR code for a security update.
7. Account update required email
The email below claims to be from Xfinity and informs the recipient that their Xfinity home system is offline. The pictures appear to be broken and don’t load along with the email. The user is asked to immediately update important account information to restore the account. On clicking the “Update Information Now” button, the user is redirected to a fake website that collects sensitive information that can be used for various scams.
Why you should be suspicious:
- The logo of the company is wrong.
- The email uses complex language that is uncharacteristic of the company.
- The broken image name shows as ‘Xfinit’ instead of the brand name.

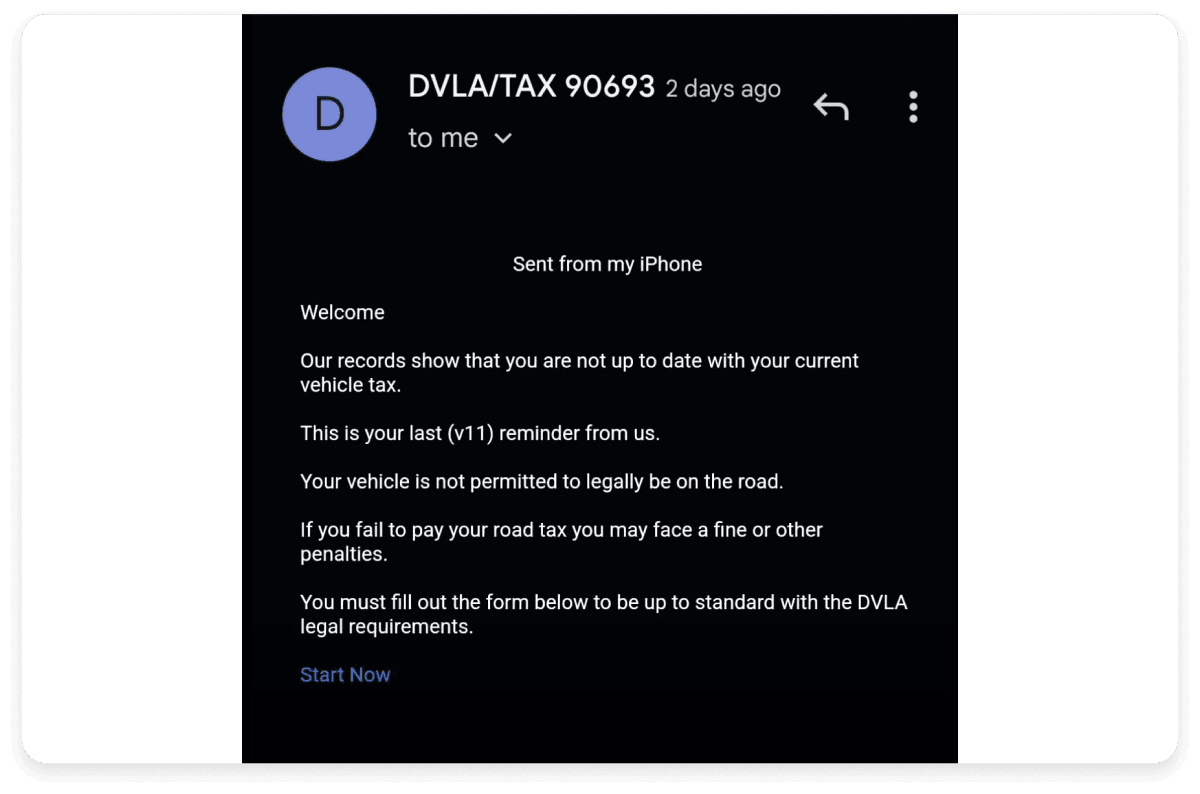
8. Vehicle tax email
The following email pretends to be sent from a government agency and informs the user that they have not paid their vehicle tax. It provides the user with a link to a form to fill to help avoid penalties. Once the user opens the form, they are prompted to enter all their personal and vehicle details along with their bank details. This can result in both identity theft and loss of money for the recipient.
Why you should be suspicious:
- The email is marked as “sent from my iPhone”.
- There are no details of the vehicle or the owner in the email.
- The email has very basic formatting and doesn’t have a proper CTA.
9. Failed delivery email
In the email, the recipient is informed that their package cannot be delivered. They are then redirected to a “redelivery form request” to receive the said package, which is a scam page where the user has to enter sensitive data that can be used by scammers to impersonate or steal from the user.
Why you should be suspicious:
- The button says “redelivery form request” instead of “redelivery request form”.
- The email does not contain the logo of the sender, i.e., the US Postal Service.

10. Fake invoice email
The following email is a fake invoice sent by a scammer who is spoofing Norton. The invoice informs the customer that a certain amount will be debited from their account by the end of the day. If he doesn’t want that to happen, the recipient is to call the customer support number that has been provided. On calling this number, the recipient is asked for sensitive information such as their bank account information and contact details which is then used to steal money from their account.
Why you should be suspicious:
- The email uses the wrong company logo.
- The email provides another contact number instead of simply asking the recipient to reach out to customer support.
- Norton Life Lock is written in different formats in different places.

11. Fake grant approval email
The below phishing email is sent to a college student informing that their student benefit check has been approved by their college board. To claim the supposed amount, the student is asked to provide a list of personal details including their name, contact information, and bank details, which the sender can use to steal money.
Why you should be suspicious:
- The email is not sent from an official email address.
- There are significant grammar mistakes in the body of the email.
- The email address given to reach out to is gibberish.
- The email doesn’t address the recipient by name.

Conclusion
As we have seen, phishing emails range from the laughably obvious red flags to ones that are very difficult to spot. Sometimes, they may appear to be from renowned companies like Google and Microsoft, which makes it even more difficult as these companies are usually blindly trusted by the people. Learn from these phishing attack examples to look out for alarm bells when you encounter such emails in your inbox. Generally, it is best to stay away from emails that seem too unusual, tempting, or urgent. Make sure to carry a healthy dose of skepticism and keep a keen eye for tiny details that seem out of place, and stay safe!






















